Introduction:
One of the utilities of a successful distributed ledger that enables a trustless network is its immutability: once an entry is verified, it cannot be deleted or amended retroactively. Blockchains are one such example that we will focus on. To achieve this key requirement, there are several verification methods available. One is to require there to be a “cost” of adding/modifying information to the ledger. To the extent that the cost of maliciously changing entries is uneconomical, this makes a ledger secure and deters malicious intent and contributions. Typical examples of this method are Proof of Work (POW) and Proof of Stake (POS).
For there to be such a cost, the blockchain in question must have attributed value. For the purposes of this article, we will assume this to be true, and leave the debate about the particular values of a blockchain for other discussions.

Proof of Work:
Blockchains based on Proof of Work algorithms require computational work to be done to verify new ledger entries are correct. These computed calculations are cryptographically intense and require significant energy. The incentive to perform this calculation, non-maliciously, is a transaction fee or network reward and is awarded once the majority of other participants on the network agree with the calculation. The financial cost, in this case, is the energy required to perform the calculation, and as network complexity and computational power needed increases, so does the financial cost.
The entry requirements to this are simply access to energy, computers, and software able to perform the calculation. The security of the network relies on the balance between energy expense and financial reward for malicious attacks being uneconomical. Larger networks, such as Bitcoin, are generally more secure than smaller networks since they require a larger amount of energy per calculation. Smaller networks can be potentially prone to malicious attacks at an early stage.
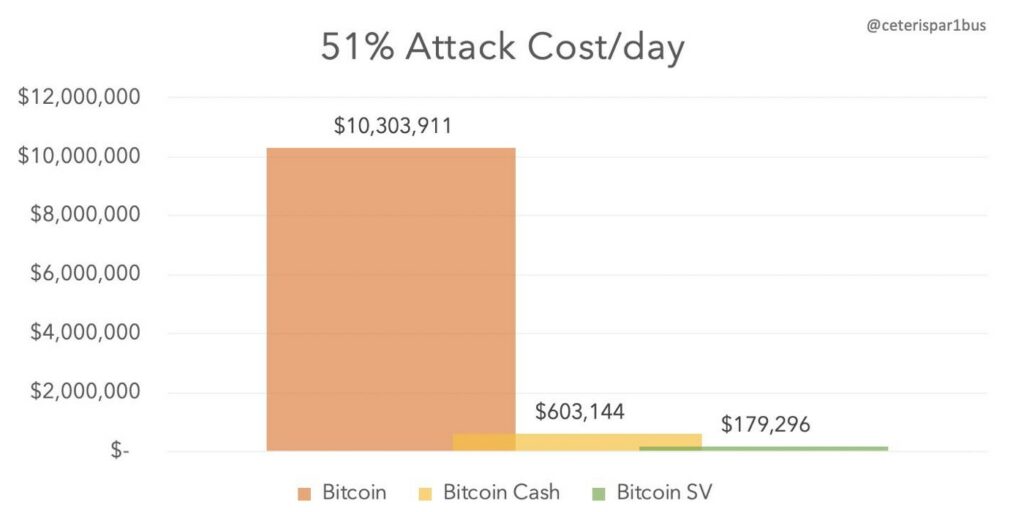
One of the benefits of this approach is anyone with access to electricity can participate in the ledger. Ideally, this should achieve a true theoretical decentralization. In practice, however, economies of scale and power price concentration tend to consolidate the decentralization. While feedback between the network reward and participation in the network should regulate some of this concentration, it is inevitable that care needs to be taken to avoid malicious software (pool) and geographical dominance.
People have criticized Proof of Work networks for its energy usage. While it may seem large, in context, it is relatively minor. For example, recent estimates have calculated the total use of energy for bitcoin since its inception is around 4.2 million tons of oil. Comparatively, the US transport industry consumes around 1–2 million tons of oil per day. Additionally, people tend to criticize a new process when it does not directly benefit them. If people knew that aluminium smelting uses about 3% of the global energy, would they reconsider purchasing their next aluminium body MacBook or IPhone?
Proof of Stake:
Blockchains based on Proof of Stake algorithms use a different method to verify additions to the ledger. The computation to cryptographically encrypt the next block is much easier but requires staking of some value to participate. In most cases, this stake is the currency of the network. Relying on game theory, the process is essentially an ante bet that each voter will back the “correct” block. If your vote goes towards the correct calculation, you receive a small reward, somewhat proportional to the transaction fee. If it goes to an incorrect block calculation, then you lose your stake. The theory is that this incentive should cause all network participants to vote for what they view as the correct encryption.
Despite the process, a PoS blockchain is still exposed to massive stakeholders being able to overwhelm the system by owning over 51% of the network if there is not sufficient decentralization. In addition, the algorithmic complexity to achieve consensus in a timely manner via this process has proven complex and as of yet even some of the largest blockchains, such as Ethereum, have not yet managed to perfect it. While this uses a lot less electricity as the computation is easier, it requires both adoption and a perfectly working algorithm.
Proof of Other:
Many business blockchains, while wishing to decentralize within a particular industry network, are more guarded from outside malicious attacks. Industries often self-regulate and have particular credentials and qualifications required for participation (finance, healthcare, pharmaceuticals to name a few). Only allowing those with accreditations or licenses to operate on the network helps to solve the malicious attack problem. Business reputation and ability to operate in the space incentivizes participants to be good actors on the network or risk losing their license. This frees up the energy requirement and allows the calculation to be computationally easier than PoW, which in turn allows for larger and faster data processing speeds on the network. However, even in this case, we see some blockchain projects establish “preferred” networks in an attempt to gain an edge over competition, while not being fully decentralizing within an industry. Participation to vote (both for governance and consensus) should be available to anyone who fits the criteria and license requirements.
One other important factor is the ease of deployment. As businesses begin to adopt blockchain into their current systems, being able to integrate on their existing systems is essential. In this case, IBM and hyperledger are capturing a significant portion of the market, with SDK meaning deployment can be fairly turnkey in a matter of weeks, not months or years.
Conclusion:
While PoW provides a process for blockchains that may be the most decentralized and secure, it is slow in speed. The criticism of energy usage for PoW is often overemphasized and comparatively better than is often portrayed. In fact, PoW security is backed by energy usage as a property of the blockchain. PoS, while potentially faster and less energy consuming, still has yet to be perfected, and its security is unknown and untested in any meaningful measure. Most current buildouts are opting for real-world penalties to incentivize good behavior. As the technology develops, we will watch closely the adoption between PoS and PoW. We expect the long term adoption will be driven by efficiencies garnered by understanding and utilizing a combination of the different verification types where appropriate.
